Introduction

In the sprawling digital metropolis of New York City, where finance, media, and global commerce converge, a new kind of sentinel stands guard. Not in a high-rise corner office, but behind a screen, defending the city's lifeblood—its data. For those with the right skills, a career in cybersecurity in NYC isn't just a job; it's a front-row seat to the future of digital defense, and it comes with a compensation package that reflects its critical importance. If you're wondering what a cyber security salary in NYC looks like, you're not just asking about a number; you're inquiring about the value of becoming a digital guardian in one of the world's most vital economic hubs. The answer is simple: the potential is immense, with average salaries comfortably cresting six figures and senior experts commanding compensation well over $250,000.
I once had a conversation with a Chief Information Security Officer (CISO) at a major Wall Street firm. She told me, "We don't just prevent data breaches; we prevent economic chaos. A single, well-executed attack on our systems could have ripple effects across the global market." That stark reality underscores why companies in New York City are willing to pay a premium for top-tier cybersecurity talent. You're not just an IT professional; you're a strategic risk manager in a high-stakes environment.
This guide is designed to be your definitive resource for understanding the cybersecurity career landscape in New York City. We will dissect salary expectations, explore the factors that drive compensation, map out the career trajectory, and provide a clear, actionable roadmap for breaking into and excelling in this dynamic field. Whether you are a student contemplating your future, a tech professional considering a pivot, or a seasoned security expert looking to maximize your earnings in the Big Apple, this article will provide the in-depth, authoritative answers you need.
### Table of Contents
- [What Does a Cybersecurity Professional in NYC Do?](#what-does-a-cybersecurity-professional-in-nyc-do)
- [Average Cyber Security Salary in NYC: A Deep Dive](#average-cyber-security-salary-in-nyc-a-deep-dive)
- [Key Factors That Influence Your Salary](#key-factors-that-influence-your-salary)
- [Job Outlook and Career Growth in NYC](#job-outlook-and-career-growth-in-nyc)
- [How to Get Started in a NYC Cybersecurity Career](#how-to-get-started-in-a-nyc-cybersecurity-career)
- [Conclusion: Is a Cybersecurity Career in NYC Right for You?](#conclusion-is-a-cybersecurity-career-in-nyc-right-for-you)
---
What Does a Cybersecurity Professional in NYC Do?

At its core, a cybersecurity professional is a protector of digital assets. In the context of New York City, this takes on a heightened significance. The "digital assets" could be the trading algorithms of a hedge fund, the personal data of millions of banking customers, the intellectual property of a leading law firm, or the critical infrastructure of the city itself. The role is multifaceted, blending technical prowess with strategic thinking and a detective's intuition.
The responsibilities are far from monolithic and vary significantly based on specialization, but they generally revolve around the core principles of the CIA Triad: Confidentiality, Integrity, and Availability.
Core Responsibilities and Daily Tasks:
- Threat Monitoring and Analysis: Using Security Information and Event Management (SIEM) systems like Splunk, QRadar, or Sentinel to monitor network traffic for suspicious activity. This involves sifting through logs, correlating events, and identifying potential threats in real-time.
- Vulnerability Management: Proactively identifying weaknesses in systems, networks, and applications. This includes running automated scans with tools like Nessus or Qualys and performing manual penetration testing to simulate real-world attacks.
- Incident Response (IR): Acting as the digital first responder when a security breach occurs. This involves containing the threat, eradicating the malware or attacker's presence, recovering systems, and conducting post-mortem analysis to prevent future incidents.
- Security Architecture and Engineering: Designing, building, and maintaining secure IT infrastructure. This could mean configuring firewalls, implementing intrusion detection/prevention systems (IDS/IPS), or securing cloud environments in AWS, Azure, or GCP.
- Governance, Risk, and Compliance (GRC): Ensuring the organization adheres to industry regulations and legal standards. In NYC, this is heavily influenced by financial regulations (e.g., NYDFS Part 500), healthcare laws (HIPAA), and data privacy acts (GDPR, CCPA). GRC analysts conduct audits, manage risk assessments, and develop security policies.
- Security Awareness Training: Educating employees to be the first line of defense. This involves running phishing simulations, creating training materials, and promoting a culture of security throughout the organization.
### A "Day in the Life" of a Mid-Level Security Analyst in a NYC Financial Firm
To make this tangible, let's walk through a typical day.
- 8:30 AM - The Morning Brief: The day begins not with coffee, but with threat intelligence. You're reviewing overnight alerts from the SIEM, checking feeds from sources like the SANS Internet Storm Center, and reading up on newly disclosed vulnerabilities (CVEs). A new strain of ransomware targeting financial services has been reported, so you immediately begin checking your firm's defenses against its specific tactics, techniques, and procedures (TTPs).
- 10:00 AM - Vulnerability Triage: The results from last night's automated vulnerability scan are in. The scanner has flagged a dozen critical vulnerabilities on public-facing web servers. Your job is to analyze these findings, determine which are true positives, and assess the risk. You create tickets in Jira for the system administrators, prioritizing the most critical fixes based on their potential impact on the business.
- 11:30 AM - The Phishing Alarm: An employee in the accounting department reports a suspicious email. You immediately pull the email into a secure sandbox environment to analyze it. It contains a malicious macro in an Excel spreadsheet. You confirm it's a targeted phishing attempt, block the sender's domain at the email gateway, and run a search to see if anyone else received it and, more importantly, clicked the link.
- 1:00 PM - Project Work: After a quick lunch at your desk, you pivot to a longer-term project: implementing a new Endpoint Detection and Response (EDR) solution. You're in a meeting with the vendor and your infrastructure team, planning the deployment schedule for the first batch of pilot users.
- 3:00 PM - Compliance Check: A GRC colleague pings you. An external auditor is coming in next week to review the firm's compliance with NYDFS Part 500 regulations. They need you to pull evidence demonstrating that access controls for critical systems are reviewed on a quarterly basis. You generate the reports from your Privileged Access Management (PAM) tool.
- 4:30 PM - Log Review and Reporting: You spend the last hour of your day reviewing access logs for critical databases, looking for any anomalous patterns. You document the day's activities, update your incident tickets, and prepare a brief summary for the daily security stand-up meeting the next morning. You leave the office knowing that your vigilance helped protect billions of dollars in assets for another day.
---
Average Cyber Security Salary in NYC: A Deep Dive
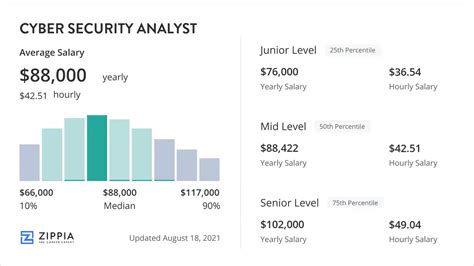
New York City is consistently ranked as one of the highest-paying metropolitan areas for cybersecurity professionals in the United States, second only to the San Francisco Bay Area in many surveys. The high cost of living is certainly a factor, but the primary drivers are the immense concentration of high-value industries (especially finance) and the relentless demand for elite talent.
To provide a comprehensive picture, it's essential to look at data from multiple authoritative sources. It's important to note that job titles can be fluid ("Information Security Analyst," "Cyber Security Engineer," "Security Consultant"), but they all fall under the broader cybersecurity umbrella.
According to the U.S. Bureau of Labor Statistics (BLS), the national median pay for Information Security Analysts was $120,360 per year as of May 2023. However, the BLS also provides metropolitan area data, which shows the New York-Newark-Jersey City, NY-NJ-PA metropolitan area boasts an annual mean wage of $144,470. This immediately highlights the significant "NYC premium."
Let's break this down further using data from reputable salary aggregators, which often provide a more real-time and granular view.
- Salary.com reports that the average Cyber Security Analyst salary in New York, NY, is $107,322, but notes the typical range falls between $92,261 and $124,311. For a more senior role like a "Cyber Security Manager," the average jumps to $158,110, with a range typically between $141,602 and $176,140. This illustrates the strong financial incentive for career progression.
- Glassdoor, which aggregates self-reported data, shows the average total pay for a "Cyber Security Analyst" in New York City is $129,584 per year, with a likely range of $101,000 to $167,000. This "total pay" figure includes an estimated base salary of $109k and additional pay (bonuses, profit sharing) of around $21k.
- Payscale estimates the average salary for a Cyber Security Analyst in New York, NY, at $96,629, but this number can be misleading as it may include more entry-level roles. Their data shows a range from $67,000 to $145,000 for base salary alone.
Synthesizing this data, we can establish a reliable baseline: a mid-level cybersecurity professional in NYC can expect a base salary in the $110,000 to $145,000 range, with total compensation being significantly higher.
### Salary Brackets by Experience Level in NYC
Experience is the single most significant determinant of salary. Here's a detailed breakdown of what you can expect at different stages of your career in New York City.
| Experience Level | Years of Experience | Typical Base Salary Range (NYC) | Total Compensation Insights | Common Roles |
| :--- | :--- | :--- | :--- | :--- |
| Entry-Level | 0-2 years | $85,000 - $115,000 | Bonuses are less common but may include a small signing bonus or performance-based annual bonus (~5%). | Security Operations Center (SOC) Analyst, Junior InfoSec Analyst, IT Auditor |
| Mid-Career | 3-7 years | $115,000 - $160,000 | Annual bonuses become standard (10-20% of base salary). Equity may be offered at startups or tech firms. | Cyber Security Analyst, Security Engineer, Penetration Tester, GRC Analyst |
| Senior | 8-15 years | $160,000 - $220,000+ | Substantial bonuses (20-35%+). Significant equity, stock options, or RSUs, especially in public companies. | Senior Security Engineer, Security Architect, Threat Intelligence Lead, Incident Response Manager |
| Expert/Leadership| 15+ years | $220,000 - $400,000+ | Executive-level compensation. Large bonuses, significant equity stakes, and long-term incentive plans (LTIPs). | Director of Security, Principal Security Architect, Chief Information Security Officer (CISO) |
*Data synthesized from BLS, Salary.com, Glassdoor, and industry reports as of early 2024.*
### Beyond the Base Salary: Understanding Total Compensation
In a competitive market like NYC, base salary is only one piece of the puzzle. High-paying roles, especially in finance and big tech, come with a robust compensation package:
- Annual Bonuses: This is the most common form of variable pay. In finance, bonuses are legendary and can sometimes equal 50-100% or more of the base salary for high-performers in critical roles (like security for a trading desk). In other industries, a 15-25% bonus is more typical for senior roles.
- Stock Options / Restricted Stock Units (RSUs): Prevalent in publicly traded tech companies and mature startups, equity is a powerful wealth-building tool. RSUs are grants of company stock that vest over time, while options give you the right to buy stock at a predetermined price.
- Profit Sharing: Some companies, particularly private ones, distribute a portion of their profits to employees.
- Signing Bonuses: Often used to lure top talent, a signing bonus of $10,000 to $50,000 (or more) is common for senior hires in NYC.
- Benefits and Perks: While not direct cash, the value is significant. This includes top-tier health insurance (with low premiums/deductibles), generous 401(k) matching (often 5-7%), paid parental leave, wellness stipends, and substantial budgets for training and certifications.
When evaluating a job offer in NYC, it is absolutely critical to look at the total compensation and not just the base salary figure. An offer with a $150,000 base and a guaranteed 25% bonus is superior to a $170,000 base with no bonus potential.
---
Key Factors That Influence Your Salary

Your potential cyber security salary in NYC is not a fixed number. It's a dynamic figure influenced by a complex interplay of your background, skills, and the specific context of the job. Understanding these levers is key to maximizing your earning potential. This section, the most detailed in our guide, will dissect each of those factors.
###
Level of Education
While cybersecurity is a field where skills and experience can often trump formal education, a degree still sets a strong foundation and influences starting salaries.
- Associate's Degree: An Associate's degree in Cybersecurity or Information Technology can be a ticket to entry-level roles, such as a SOC Analyst Tier 1 or a help desk technician with security responsibilities. However, you'll likely start at the lower end of the salary spectrum (e.g., $75k-$90k in NYC) and will need to supplement with certifications to advance.
- Bachelor's Degree: This is the standard expectation for most corporate roles. A Bachelor of Science (B.S.) in Computer Science, Information Technology, or a dedicated Cybersecurity program is most desirable. Graduates from reputable programs can command starting salaries at the higher end of the entry-level bracket ($95k+). A degree demonstrates a foundational understanding of networking, operating systems, and programming, as well as a commitment to a multi-year learning path.
- Master's Degree: A Master's degree in Cybersecurity (e.g., from NYU's Tandon School of Engineering) or an MBA with a concentration in Information Systems can significantly boost earning potential, particularly for leadership or specialized GRC roles. It signals advanced, specialized knowledge. A candidate with a Master's might bypass some entry-level steps or command a 10-15% higher salary than a Bachelor's-only counterpart for the same role. It is almost a prerequisite for many senior management and C-suite positions.
- Cybersecurity Bootcamps: Intensive, short-term bootcamps (e.g., from providers like Flatiron School or Fullstack Academy) have become a popular alternative pathway. They offer focused, hands-on training. While they can successfully land graduates their first job, initial salaries might be slightly lower than those for four-year degree holders. Their primary value is in a rapid career pivot, and a graduate's success will heavily depend on their portfolio of projects and networking efforts.
###
Years of Experience
As illustrated in the salary table, experience is the paramount factor. The value of a cybersecurity professional grows exponentially as they move from theory to practice.
- 0-2 Years (The Foundation): At this stage, you are learning the ropes. Your value is in your ability to learn quickly, follow procedures, and handle high-volume, lower-complexity tasks like monitoring alerts and patching systems. Salary growth is tied to mastering the fundamental tools (SIEM, vulnerability scanners) and gaining your first critical certifications (like CompTIA Security+).
- 3-7 Years (The Specialist): You are no longer just following a playbook; you are starting to write it. You've experienced real incidents, developed a specialty (e.g., cloud security, incident response), and can work with significant autonomy. This is where salaries see the sharpest increase. You can lead small projects, mentor junior analysts, and your opinion carries weight. You've likely earned an intermediate certification like the CYSA+ or CEH.
- 8-15+ Years (The Strategist/Architect): At this level, your value is strategic. You're not just fixing problems; you're designing systems to prevent them entirely. You understand the business context of security risks and can communicate them to leadership. As a Security Architect, you design enterprise-wide security solutions. As a manager, you lead teams and control budgets. Earning the CISSP (Certified Information Systems Security Professional) is a near-universal milestone at this stage and acts as a significant salary multiplier. Your salary is now in the top echelons, reflecting your deep expertise and impact on the organization's risk posture.
###
Geographic Location (The NYC Premium)
While this guide focuses on NYC, it's crucial to understand *why* it pays so well compared to other areas.
- New York City vs. National Average: As established, the mean salary for an Information Security Analyst in the NYC metro area ($144,470) is roughly 20% higher than the national median ($120,360). This premium accounts for the higher cost of living and, more importantly, the concentration of high-stakes industries.
- NYC vs. Other Tech Hubs: NYC is in a constant battle for talent with other major tech hubs.
- San Francisco Bay Area: Often the only metro that outpays NYC, driven by the sheer density of "Big Tech" headquarters and venture-backed startups offering lucrative equity packages.
- Washington, D.C. Metro: A strong competitor due to the massive federal government and contractor ecosystem. Salaries are high, particularly for those with security clearances.
- Austin, TX / Seattle, WA: Growing tech hubs with strong demand and high salaries, though typically still a notch below NYC and the Bay Area.
- NYC vs. Lower Cost of Living (LCOL) Areas: A cybersecurity professional in a city like Kansas City or Raleigh might earn $90,000 for a role that pays $130,000 in NYC. While the NYC salary is higher in absolute terms, the purchasing power must be considered. However, for sheer career trajectory and access to the most complex and high-paying jobs, NYC remains a top destination.
Within NYC itself, location is less of a factor for salary, but the *commute* can be a major lifestyle consideration. Jobs in Manhattan, particularly Midtown and the Financial District, are the most plentiful and often the highest-paying.
###
Company Type & Size
The type of company you work for dramatically impacts your compensation structure and work environment.
- Finance (Investment Banks, Hedge Funds, FinTech): This is the apex predator of the NYC cybersecurity job market. Firms like Goldman Sachs, JPMorgan Chase, and major hedge funds view cybersecurity as a core business function, not an IT cost center. They pay absolute top-of-market salaries and offer enormous bonuses because the cost of a breach is catastrophic. The work is high-pressure and demanding, with a strong focus on low-latency security, trading system protection, and rigorous regulatory compliance.
- Large Tech Companies (Google, Amazon, Meta): These companies have a major presence in NYC and compete directly with finance for top talent. Compensation is heavily weighted towards a combination of high base salary and substantial RSU grants that vest over time. The culture is often engineering-driven, focusing on building scalable, automated security solutions for massive infrastructure.
- Consulting / Professional Services (Big Four, Boutique Firms): Firms like Deloitte, PwC, EY, and KPMG, as well as specialized security consultancies like Mandiant or CrowdStrike, hire vast numbers of security professionals. As a consultant, you'll work on projects for a variety of clients, offering exposure to different industries. The pay is very competitive, but the lifestyle can involve significant travel and long hours. Your salary is tied to your billable rate.
- Startups: A venture-backed startup offers a different proposition. The base salary might be slightly lower than at a large corporation, but this is often offset by a significant grant of stock options. This is a high-risk, high-reward scenario: if the company succeeds, your equity could be worth a fortune. The work is fast-paced, and you'll likely wear many hats.
- Government and Non-Profit: Roles with city (e.g., NYC Cyber Command), state, or federal agencies, as well as universities and hospitals, offer lower base salaries than the private sector. However, they compensate with exceptional job security, excellent pensions, and a better work-life balance. These roles are driven by public service and the mission of protecting critical city or national infrastructure.
###
Area of Specialization
"Cybersecurity" is a vast field. Specializing in a high-demand niche is one of the most effective ways to increase your value.
| Specialization | Description | Typical NYC Salary Range (Mid-to-Senior) | Why It Pays Well |
| :--- | :--- | :--- | :--- |
| Cloud Security Engineer | Secures cloud environments (AWS, Azure, GCP). Focuses on IAM, network security groups, container security (Docker/Kubernetes), and automation. | $150,000 - $230,000+ | The entire world is moving to the cloud. Expertise is scarce and critical for every modern company. |
| Penetration Tester / Offensive Security| "Ethical Hacker." Hired to legally break into systems to find vulnerabilities before real attackers do. Requires deep technical skill and creativity. | $140,000 - $210,000+ | Directly demonstrates and reduces business risk. Highly specialized and technical skill set. |
| Application Security (AppSec) Engineer| Works with developers to secure software throughout the development lifecycle (DevSecOps). Finds and fixes flaws in code. | $160,000 - $240,000+ | Securing proprietary software is a top priority. Blends development and security skills, which is a rare combination. |
| Security Architect| Designs the organization's entire security framework. A strategic, high-level role requiring deep experience across multiple domains. | $180,000 - $260,000+ | Their decisions have a massive, long-term impact on the company's security posture and budget. |
| Incident Response (IR) / Forensics| The "firefighters." They investigate breaches, perform digital forensics to determine the root cause, and lead recovery efforts. | $145,000 - $220,000+ | High-stress, high-impact role. Expertise is essential during a company's worst moments. Often involves on-call duties. |
| GRC / Security Risk Analyst| Focuses on policy, compliance, and risk management. Less technical, more strategic. Crucial in regulated industries like finance. | $120,000 - $190,000+ | Directly addresses legal and financial risk from regulators. Essential for passing audits and avoiding fines. |
###
In-Demand Skills
Beyond job titles, specific skills can make your resume stand out and justify a higher salary.
- Technical Skills:
- Cloud Platforms: Deep knowledge of AWS, Azure, or GCP is arguably the most sought-after skill today. Certifications like AWS Certified Security - Specialty are golden tickets.
- Scripting and Automation: Proficiency in Python is the de facto standard. The ability to automate security tasks (e.g., parsing logs, orchestrating responses) is a massive force multiplier.
- SIEM and EDR Expertise: Mastery of tools like Splunk, Sentinel, CrowdStrike Falcon, or SentinelOne. It's not just about using the tool, but building custom dashboards, alerts, and playbooks.
- Network Security: A deep, fundamental understanding of TCP/IP, routing, firewalls, and protocols.
- Container and Orchestration Security: Skills in securing Docker, Kubernetes, and serverless functions are on the cutting edge of demand.
- Soft Skills:
- Communication: The ability to explain complex technical risk in simple business terms to a non-technical audience (e.g., a board of directors) is a skill that separates senior professionals from junior ones.
- Problem-Solving: A logical, analytical, and calm approach to solving complex problems under pressure is the essence of incident response and threat hunting.
- Business Acumen: Understanding how the business makes money and how security risks can impact revenue, reputation, and operations. This allows you to prioritize efforts effectively.
---
Job Outlook and Career Growth in NYC

The job outlook for cybersecurity professionals, both nationally and in New York City, is nothing short of explosive. It's one of the few fields where the demand for qualified candidates drastically outstrips the supply, creating a favorable market for job seekers.
The U.S. Bureau of Labor Statistics projects that employment for Information Security Analysts will grow by 32 percent from 2022 to 2032. This is described as "much faster than the average for all occupations." The BLS estimates this will result in about 16,800 openings for information security analysts each year, on average, over the decade. These openings are expected to result from the need to replace workers who transfer to different occupations or exit the labor force, as well as from new jobs being created.
In New York City, this trend is amplified. The city is not just a hub but an epicenter for industries that are prime targets for cyberattacks:
- Wall Street: The constant threat of financial fraud, data theft, and market manipulation drives relentless hiring.
- Media and Advertising: Protection of intellectual property and subscriber data
