In the sprawling digital landscape of the 21st century, where data is the new oil and connectivity is the new currency, a silent war is waged every second of every day. This is the world of cybersecurity, and its professionals are the digital guardians standing between order and chaos. If you're drawn to a career that is not only intellectually stimulating and mission-critical but also exceptionally lucrative, particularly in a booming economic powerhouse like the Lone Star State, you've come to the right place.
This guide is designed to be your definitive resource, answering the crucial query: "What is the typical cyber security salary in Texas?" We will move far beyond a simple number, providing a granular, data-backed analysis of what you can expect to earn, the factors that will command a higher paycheck, and the precise steps you need to take to launch or advance your career in this dynamic field. The demand for skilled cybersecurity professionals in Texas is surging, fueled by the state's explosive growth in the tech, finance, energy, and healthcare sectors. The median salary for these roles often surpasses the six-figure mark, with top earners commanding compensation well over $200,000.
I once counseled a mid-career IT helpdesk technician from Houston who felt his career had plateaued. He was brilliant at problem-solving but yearned for a role with greater impact and financial reward. After a focused year of upskilling, earning key certifications, and building a home lab, he landed an entry-level Security Operations Center (SOC) Analyst role; within three years, he had more than doubled his previous salary and is now a respected security engineer for a major energy firm. His story is a testament to the fact that with the right strategy, a career in Texas cybersecurity is not just a job—it's a gateway to professional fulfillment and financial security.
This article will serve as your strategic blueprint. We will dissect every component that contributes to your earning potential, from education and certifications to your specific location within Texas and the type of company you work for.
### Table of Contents
- [What Does a Cyber Security Professional in Texas Do?](#what-they-do)
- [Average Cyber Security Salary in Texas: A Deep Dive](#salary-deep-dive)
- [Key Factors That Influence Your Salary](#key-factors)
- [Job Outlook and Career Growth in Texas](#job-outlook)
- [How to Get Started in a Texas Cyber Security Career](#how-to-start)
- [Conclusion: Is a Cyber Security Career in Texas Right for You?](#conclusion)
What Does a Cyber Security Professional in Texas Do?

At its core, a cybersecurity professional is a protector of digital assets. Their primary mandate is to safeguard an organization's computer systems, networks, and sensitive data from unauthorized access, attacks, damage, or theft. They are the architects of digital defense, the detectives of virtual crime scenes, and the first responders to electronic breaches. While the title "Cyber Security Analyst" is common, the field encompasses dozens of specialized roles. However, the core responsibilities remain consistent across the spectrum.
These professionals are tasked with a wide array of duties that are both proactive and reactive. Proactively, they design and implement robust security measures. This can involve configuring firewalls, deploying encryption protocols, and developing "secure by design" network architectures. They conduct regular vulnerability assessments and penetration tests (often called "ethical hacking") to find and fix weaknesses before malicious actors can exploit them. They are also educators and policymakers, training employees on security best practices and drafting the formal security policies and procedures that govern the organization.
Reactively, when a security incident occurs, they spring into action. They are responsible for incident response, which involves identifying the breach, containing the damage, eradicating the threat, and recovering the affected systems. This process often includes digital forensics—painstakingly analyzing logs, network traffic, and compromised devices to understand the "who, what, when, where, and how" of an attack. This analysis is crucial not only for recovery but also for strengthening defenses to prevent a recurrence.
### A "Day in the Life" of a Security Analyst in Austin, TX
To make this more concrete, let's imagine a day for "Maria," a mid-level Security Analyst at a growing fintech company in Austin.
- 8:30 AM: Maria arrives, grabs a coffee, and begins her day by reviewing the Security Information and Event Management (SIEM) system dashboard. The SIEM (like Splunk or QRadar) is her command center, aggregating logs from all across the company's network. She checks for any high-priority alerts that were triggered overnight—unusual login patterns, connections from suspicious IP addresses, or malware signatures.
- 9:30 AM: A Level-1 SOC analyst escalates an alert. An employee's credentials appear to be logging in from both Dallas and a foreign country within minutes of each other—a classic "impossible travel" scenario. Maria begins her investigation. She temporarily suspends the account to prevent further access, contacts the employee to verify their activity, and starts digging into the logs to trace the origin of the foreign IP address.
- 11:00 AM: The investigation confirms the employee was the victim of a phishing attack. Maria works with the IT team to ensure the user's machine is clean and helps them reset all their credentials. She then documents the incident meticulously, noting the tactics used by the attacker.
- 12:00 PM: Lunch. She often uses this time to read industry blogs like Krebs on Security or The Hacker News to stay current on new threats.
- 1:00 PM: Maria pivots to a proactive project: conducting a vulnerability scan on a new set of servers being prepared for deployment. She uses a tool like Nessus to scan the servers for known vulnerabilities, misconfigurations, or missing patches.
- 2:30 PM: The scan is complete. Maria analyzes the report, prioritizing the vulnerabilities by severity. She creates tickets for the systems administration team, providing clear instructions on how to remediate the critical and high-risk findings before the servers go live.
- 4:00 PM: Maria joins a meeting with the software development team. They are planning a new application feature, and she is there to provide security requirements, ensuring that security is "baked in" from the start, not "bolted on" as an afterthought. This is a key part of the "Shift Left" security philosophy.
- 5:00 PM: Before logging off, Maria does one last check of the SIEM dashboard and reviews her notes for the day. She updates the incident report from the morning and plans her priorities for tomorrow, which include drafting a company-wide alert about the new phishing campaign she uncovered.
This blend of reactive investigation and proactive hardening is the essence of the cybersecurity role in Texas and beyond. It’s a field where no two days are exactly alike and where your work has a direct and tangible impact on your organization's safety and success.
Average Cyber Security Salary in Texas: A Deep Dive
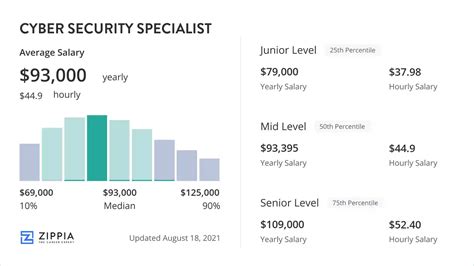
Let's address the central question: How much can you earn in cybersecurity in Texas? The financial prospects are exceptionally strong, reflecting the critical demand for these skills. Texas consistently ranks as one of the top states for both employment level and compensation in the cybersecurity field.
According to the most recent data from the U.S. Bureau of Labor Statistics (BLS) Occupational Employment and Wage Statistics (OEWS), the annual mean wage for Information Security Analysts in Texas is $124,110 (as of May 2023). This is significantly higher than the median household income in the state and places cybersecurity firmly in the upper echelon of professional careers.
However, a single average doesn't tell the whole story. The compensation you can expect is highly dependent on your experience, role, and a variety of other factors we will explore in the next section. To provide a more realistic picture, let's break down the salary range.
- National Average Comparison: The national annual mean wage for this role is $124,740. This shows that the cyber security salary in Texas is right in line with the robust national average, making it a competitive market without the extreme cost-of-living pressures of places like Silicon Valley or New York City.
### Salary by Experience Level in Texas
Salary growth in cybersecurity is steep and rapid for those who demonstrate skill and commitment. Here is a breakdown of typical salary brackets you can expect at different stages of your career in Texas, based on an aggregation of data from the BLS, Salary.com, and Glassdoor.
| Experience Level | Years of Experience | Typical Salary Range (Texas) | Key Responsibilities & Titles |
| :--- | :--- | :--- | :--- |
| Entry-Level | 0-2 Years | $75,000 - $95,000 | Monitoring alerts, running scans, tier-1 incident response. Titles: SOC Analyst, Jr. Security Analyst, IT Security Specialist. |
| Mid-Career | 3-8 Years | $95,000 - $140,000 | Deeper analysis, threat hunting, policy implementation, managing security tools. Titles: Security Analyst, Security Engineer, Penetration Tester. |
| Senior/Lead | 8-15 Years | $140,000 - $185,000+ | Leading projects, designing security architecture, mentoring junior staff, threat intelligence. Titles: Senior Security Engineer, Security Architect, Lead Incident Responder. |
| Managerial/Executive| 10+ Years | $170,000 - $250,000+ | Strategy, budget management, team leadership, compliance oversight, reporting to executives. Titles: Security Manager, Director of Security, CISO. |
*(Source: Data compiled and synthesized from BLS OEWS, Salary.com, and Glassdoor for Texas metro areas, May 2024.)*
Important Note on BLS Data: The BLS data for Texas shows a wide spectrum. The 10th percentile (representing entry-level positions) earns around $78,020, while the 90th percentile (representing the most experienced and specialized senior professionals) earns $189,520 or more. This highlights the immense growth potential within the field.
### Beyond the Base Salary: Understanding Total Compensation
A discussion about a cyber security salary in Texas would be incomplete without looking at the total compensation package. Your base salary is just one piece of the puzzle. Companies, especially in the competitive tech and finance sectors, use a variety of incentives to attract and retain top talent.
- Annual Bonuses: Performance-based bonuses are extremely common. These can range from 5% of your base salary at the junior level to over 30% for senior and managerial roles. A mid-career analyst with a $120,000 base salary might receive a 10-15% bonus, adding an extra $12,000-$18,000 to their annual earnings.
- Stock Options/RSUs: Particularly prevalent in publicly traded companies and tech startups, restricted stock units (RSUs) or stock options can be a significant part of your compensation. This gives you an equity stake in the company's success.
- Profit Sharing: Some companies, especially in finance and consulting, offer profit-sharing plans where a portion of the company's profits is distributed among employees.
- Sign-On Bonuses: To entice top candidates in a tight labor market, companies in Austin, Dallas, and Houston frequently offer sign-on bonuses, which can range from a few thousand dollars to $20,000 or more for highly sought-after roles.
- Benefits and Perks: Do not underestimate the value of a strong benefits package. This includes comprehensive health, dental, and vision insurance; a strong 401(k) matching program (e.g., a 100% match up to 6% of your salary); and a generous paid time off (PTO) policy. Furthermore, a key perk in this field is a professional development budget. Many Texas companies will pay for expensive training and certification exams (like the SANS courses or CISSP exam), which are investments in your skills that can cost thousands of dollars.
When evaluating a job offer, it's crucial to calculate the value of the entire package, not just the base salary number. A role with a slightly lower base but with a significant bonus potential and a fully-funded training budget may be far more valuable in the long run.
Key Factors That Influence Your Salary

While we've established a strong baseline for a cyber security salary in Texas, your individual earnings will be determined by a specific set of factors. Mastering these levers is the key to maximizing your income potential. As a career analyst, I've seen professionals strategically navigate these areas to accelerate their salary growth far beyond the average.
### `
`1. Level of Education and Certifications`
`Your formal education and, more importantly, your professional certifications are foundational to your credibility and earning power.
Education:
A bachelor's degree is typically the minimum requirement for most mid-level cybersecurity roles. Degrees in Computer Science, Information Technology, or Management Information Systems are the most common and valued. They provide the essential knowledge of networking, operating systems, and programming that cybersecurity is built upon.
Does a Master's degree help? Yes, significantly. A Master of Science in Cybersecurity or a related field can provide a substantial salary boost, often in the range of 10-15%. It qualifies you for more senior, strategic, and research-oriented roles. Furthermore, it can often substitute for a few years of experience in the eyes of hiring managers, allowing you to enter the field at a higher level. An MBA with a technology or security focus is also highly valuable for those aspiring to leadership positions like Chief Information Security Officer (CISO).
Certifications (The Great Equalizer):
In cybersecurity, certifications are arguably more impactful on salary than the prestige of your university. They are standardized, verifiable proof of your skills in specific domains. A candidate with a state university degree but holding a prestigious certification like the CISSP will often be chosen over an Ivy League graduate with no certifications.
Here's a hierarchy of certifications and their impact on salary:
- Foundational (Required for Entry):
- CompTIA Security+: This is the universal starting point. It validates core security knowledge and is often a hard requirement for both government and corporate jobs. Having this can be the difference between getting an interview and being filtered out by HR software.
- Intermediate (Salary Boosters):
- GIAC Security Essentials (GSEC): Respected and hands-on, from the SANS Institute.
- Certified Ethical Hacker (CEH): Focuses on offensive security tools and techniques. Popular for those wanting to become penetration testers.
- CompTIA CySA+ (Cybersecurity Analyst): A more advanced analytical certification, focusing on threat detection and response.
- Advanced/Expert (Major Salary Drivers):
- Certified Information Systems Security Professional (CISSP): This is the gold standard. It is a management-level certification that requires a minimum of five years of paid work experience. Earning a CISSP is one of the single most effective ways to significantly increase your salary, often by $20,000 or more per year. It signals to employers that you have both deep and broad knowledge across multiple security domains.
- Certified Information Security Manager (CISM): Similar in prestige to the CISSP but focused more on the governance and program management side of security. Essential for aspiring security managers and directors.
- Certified Information Systems Auditor (CISA): The premier certification for security auditors and GRC (Governance, Risk, and Compliance) professionals.
- Offensive Security Certified Professional (OSCP): A highly respected, hands-on certification for penetration testers that requires passing a grueling 24-hour practical exam. Holding an OSCP can command a premium salary due to its difficulty and practical relevance.
### `
`2. Years and Quality of Experience`
`Experience is the single most significant factor in determining your salary. As shown in the table above, compensation grows dramatically as you move from an entry-level analyst to a senior architect or manager. However, it's not just the number of years that matters, but the *quality* and *relevance* of that experience.
- 0-2 Years (The Foundation): Your goal is to absorb as much as possible. Experience in a Security Operations Center (SOC) is invaluable, as you'll be exposed to a high volume of alerts and incidents. You're paid to learn and execute established procedures.
- 3-8 Years (The Specialization): This is where you transition from being a generalist to a specialist. You start leading small projects, mentoring junior analysts, and developing deep expertise in a specific tool (like a SIEM) or a process (like threat hunting or digital forensics). Your salary increases as your autonomy grows and you become the "go-to" person for a particular area.
- 8+ Years (The Strategist/Leader): At this stage, you are no longer just solving technical problems; you are solving business problems. Senior professionals are expected to think strategically, design security programs, manage risk, influence business decisions, and lead teams. Your value is measured by your ability to reduce organizational risk and enable the business to operate securely. This strategic impact is what commands salaries north of $150,000-$200,000.
### `
`3. Geographic Location Within Texas`
`While we've discussed the Texas state average, where you work within the state matters immensely. The cost of living and, more importantly, the concentration of high-paying industries create significant salary variations between metropolitan areas.
Here’s a comparative look at the major Texas hubs, with data derived from BLS OEWS (May 2023) and Salary.com (2024):
| Metropolitan Area | Annual Mean Wage (BLS) | Key Industries & Notes |
| :--- | :--- | :--- |
| Dallas-Fort Worth-Arlington | $126,920 | A massive and diverse economic hub. Strong in Finance, Banking, Defense Contracting, and Corporate Headquarters. High demand for GRC, application security, and corporate security roles. |
| Austin-Round Rock | $129,590 | The tech heart of Texas, often called "Silicon Hills." Dominated by Big Tech, startups, and software companies. Highest demand for Cloud Security, Product Security, and Application Security engineers. Often has the highest salaries due to intense competition for talent. |
| Houston-The Woodlands-Sugar Land | $122,250 | The global center for the Energy (Oil & Gas) and Healthcare sectors. High demand for specialists in Industrial Control Systems (ICS) / Operational Technology (OT) security and HIPAA compliance experts. |
| San Antonio-New Braunfels | $118,120 | A major center for Military/Government/Defense and Financial Services. Home to Joint Base San Antonio, the NSA's Texas Cryptologic Center, and major HQs for USAA and Valero. Strong demand for cleared professionals (holding a security clearance) and government contracting roles. |
Analysis:
- Austin and Dallas typically lead in overall salary potential due to the high concentration of tech and finance companies competing for a limited pool of elite talent.
- Houston offers unique, high-paying opportunities for those specializing in OT/ICS security, a critical and niche field.
- San Antonio is the clear leader for those with or able to obtain a U.S. government security clearance. These "cleared" roles often come with a significant salary premium (a "clearance bump") due to the small supply of qualified candidates.
### `
`4. Company Type and Size`
`The type of organization you work for has a profound impact on both your salary and your day-to-day experience.
- Large Enterprises / Fortune 500 (e.g., AT&T, Dell, Texas Instruments): These companies, plentiful in the DFW area, typically offer the highest base salaries, structured bonus plans, and exceptional benefits. The roles are often more specialized and siloed. You might be a "Firewall Engineer" or an "Identity and Access Management Specialist."
- Tech Startups (e.g., Austin's vibrant startup scene): The base salary might be slightly lower than at a large enterprise, but this is often compensated for with significant stock options. The work environment is fast-paced, with broader responsibilities. A single analyst might handle everything from cloud security to incident response. High risk, high reward.
- Government / Defense Contractors (e.g., working for DoD at Fort Sam Houston): Base salaries can be lower than in the private sector. However, this is balanced by incredible job stability, excellent federal benefits (pensions), and a strong work-life balance. As mentioned, possessing a security clearance (Secret, Top Secret) dramatically increases your value in this sector.
- Managed Security Service Providers (MSSPs): These companies provide security services to other businesses. The experience is fantastic, as you're exposed to many different client environments. The pay is competitive, but the work can be demanding, with on-call rotations and high-pressure client-facing responsibilities.
### `
`5. Area of Specialization`
`"Cybersecurity" is not a monolith. It's a vast field with numerous specializations, and some are far more lucrative than others due to supply and demand. As you advance in your career, specializing is the most effective way to increase your value.
- Cloud Security Engineer (Highest Demand): As companies migrate en masse to AWS, Azure, and Google Cloud, professionals who can secure these complex environments are in astronomical demand. Expertise in cloud-native security tools, Infrastructure as Code (IaC), and container security (Docker, Kubernetes) can command salaries at the very top of the scale, easily exceeding $160,000 - $200,000+ in Texas.
- Application Security (AppSec) / Product Security Engineer: These professionals work with developers to find and fix vulnerabilities in software code. With the rise of DevSecOps, their skills are critical and highly paid.
- Penetration Tester / Offensive Security: Ethical hackers who test defenses are always in demand. Specialized roles focusing on web applications, mobile, or networks can be very lucrative. OSCP certification is a major differentiator here.
- Threat Intelligence Analyst: These analysts research threat actors, their tactics, techniques, and procedures (TTPs) to provide proactive intelligence to the organization. It's a highly analytical role that blends technical skill with research and writing.
- Governance, Risk, and Compliance (GRC): GRC analysts focus on the business side of security. They ensure the company complies with regulations (like SOX, GDPR, HIPAA), manage risk frameworks (like NIST), and conduct audits. While perhaps less "hands-on-keyboard," senior GRC professionals and managers are vital and well-compensated.
- Incident Responder / Digital Forensics: When a breach happens, these are the experts who are called in. It's a high-stress, high-reward specialization that requires deep technical knowledge and a calm, methodical approach under pressure.
### `
`6. In-Demand Skills (The Salary Boosters)`
`Beyond your title, a specific set of high-value skills can add thousands to your salary offers. If you can demonstrate proficiency in these areas on your resume and in interviews, you will stand out.
- Cloud Platform Expertise (AWS, Azure, GCP): You must list specific services you've worked with (e.g., AWS Security Hub, Azure Sentinel, IAM, VPC configurations).
- Scripting and Automation (Python): The ability to automate repetitive tasks using Python or another scripting language is a massive force multiplier. It shows you can scale security operations and is often a prerequisite for senior roles.
- SIEM and SOAR Expertise (Splunk, QRadar, Palo Alto Cortex XSOAR): Deep knowledge of a major SIEM platform, including the ability to write custom queries, build dashboards, and create alerts, is highly valued. SOAR (Security Orchestration, Automation, and Response) is the next level.
- Understanding of Frameworks (NIST CSF, ISO 27001, MITRE ATT&CK): Speaking the language of industry frameworks demonstrates strategic understanding. MITRE ATT&CK, in particular, has become the common language for describing adversary behavior.
- Soft Skills: Do not underestimate these. The ability to communicate complex technical issues to non-