Table of Contents

- [What Does a Cybersecurity Professional with a Master's Degree Do?](#what-does-a-cybersecurity-professional-with-a-masters-degree-do)
- [Average masters in cyber security salary: A Deep Dive](#average-masters-in-cyber-security-salary-a-deep-dive)
- [Key Factors That Influence Your masters in cyber security salary](#key-factors-that-influence-your-masters-in-cyber-security-salary)
- [Job Outlook and Career Growth in Cybersecurity](#job-outlook-and-career-growth-in-cybersecurity)
- [How to Get Started on This High-Value Career Path](#how-to-get-started-on-this-high-value-career-path)
- [Conclusion: Is a Master's in Cybersecurity Worth It?](#conclusion-is-a-masters-in-cybersecurity-worth-it)
---
In a world run on data, where digital infrastructure is the bedrock of our global economy, a new kind of hero has emerged: the cybersecurity professional. These are the digital guardians, the strategic thinkers, and the technical wizards standing between order and chaos. If you're reading this, you likely feel the pull of this critical, high-stakes field. You're not just looking for a job; you're looking for a mission—a career that is not only intellectually stimulating and impactful but also financially rewarding. The question that naturally follows is a pragmatic one: what is the real-world value of advanced education in this domain? Specifically, what does a masters in cyber security salary look like in today's market?
The answer is, in a word, exceptional. For professionals armed with a master's degree, a six-figure salary isn't an endpoint; it's often the starting point. We're talking about a typical range from $90,000 to well over $250,000 per year, depending on a host of factors we will explore in exhaustive detail.
I once sat down with the Chief Information Security Officer (CISO) of a major financial institution who told me, "I don't hire people just to run tools. I hire them to solve problems we haven't even discovered yet." That single sentence perfectly encapsulates the value of a master's degree; it trains you not just to be a technician but a strategist, a leader, and a forward-thinking problem solver—qualities that organizations are willing to pay a significant premium for.
This guide is designed to be your definitive resource. We will move beyond simple salary numbers and dissect every element that contributes to your earning potential. We'll explore job roles, the powerful impact of location and specialization, the jaw-dropping job outlook, and a step-by-step roadmap to get you started. This is not just an article; it's the blueprint for your future as a leader in cybersecurity.
What Does a Cybersecurity Professional with a Master's Degree Do?

A master's degree in cybersecurity is not a job title itself, but rather a powerful accelerator that qualifies you for advanced and leadership roles within the security ecosystem. While a bachelor's degree might land you a role as a Tier 1 SOC Analyst, a master's degree primes you for positions that require a deeper understanding of risk management, security architecture, policy development, and strategic leadership.
At its core, the job is to protect an organization's most valuable digital assets. This includes customer data, intellectual property, financial records, and the operational technology that keeps the business running. It's a proactive and reactive field, blending meticulous planning with rapid-fire crisis management.
Core Responsibilities of an Advanced Cybersecurity Professional:
- Security Architecture and Design: You won't just be operating security tools; you'll be designing the systems. This involves creating a resilient security framework that integrates with business objectives, selecting the right technologies, and ensuring they are implemented correctly across networks, cloud environments, and applications.
- Risk Management and Governance: This is a key differentiator for master's-level professionals. It involves identifying, assessing, and mitigating security risks. You'll conduct risk assessments, develop security policies and procedures, and ensure the organization complies with legal and regulatory standards like GDPR, HIPAA, or PCI-DSS. You'll be the one translating technical vulnerabilities into business-level risk that a board of directors can understand.
- Threat Intelligence and Hunting: Instead of waiting for alerts, you'll proactively hunt for threats within your environment. This involves analyzing threat intelligence feeds, understanding attacker tactics, techniques, and procedures (TTPs), and searching for indicators of compromise (IOCs) that may have evaded automated defenses.
- Incident Response Leadership: When a breach occurs—and it will—you will be a leader in the response effort. This goes beyond technical remediation. It involves coordinating teams, managing communication with stakeholders (including legal, PR, and executive leadership), preserving evidence for forensic analysis, and conducting post-mortems to prevent future incidents.
- Mentorship and Team Leadership: With an advanced degree comes the expectation of leadership. You'll be responsible for mentoring junior analysts, leading project teams, and potentially managing the entire security operations department.
### A "Day in the Life" of a Senior Security Engineer
To make this tangible, let's imagine a day for "Alex," a Senior Security Engineer with a Master's in Cybersecurity at a mid-sized tech company.
- 9:00 AM - 10:00 AM: Threat Briefing & Triage. Alex starts the day not by looking at a flood of low-level alerts, but by reviewing a curated threat intelligence report and conferring with the SOC team on any high-priority incidents that emerged overnight. An alert regarding unusual data exfiltration from a cloud database server catches Alex's attention.
- 10:00 AM - 12:30 PM: Proactive Threat Hunt & Deep Dive. The alert is concerning. Alex doesn't just block the IP address. Leveraging skills from a cloud security specialization, Alex dives into the cloud logs (e.g., AWS CloudTrail), cross-referencing activity with user authentication logs. Alex uses a scripting language like Python to quickly parse terabytes of data, identifying a compromised developer credential as the root cause. This is problem-solving, not just alert-clearing.
- 12:30 PM - 1:30 PM: Lunch & Continuous Learning. Over lunch, Alex reads a whitepaper from the SANS Institute on a new ransomware TTP, staying ahead of the curve.
- 1:30 PM - 3:30 PM: Architectural Review Meeting. Alex joins a meeting with the DevOps team to review the architecture for a new application. Alex acts as the security expert, pointing out the need for improved secrets management and recommending the integration of a static analysis security testing (SAST) tool into the CI/CD pipeline—a direct application of DevSecOps principles learned in the master's program.
- 3:30 PM - 5:00 PM: Incident Response & Policy Improvement. Alex finalizes the report on the morning's incident, detailing the attack path, the business impact, and the remediation steps taken. Crucially, Alex drafts a recommendation to implement mandatory multi-factor authentication (MFA) for all developer accounts with cloud access and presents this to the IT governance committee, turning a technical incident into a strategic security improvement.
This example illustrates the difference: a master's-level professional moves beyond the console to influence policy, architecture, and strategy, which is precisely why they command a higher salary.
Average masters in cyber security salary: A Deep Dive
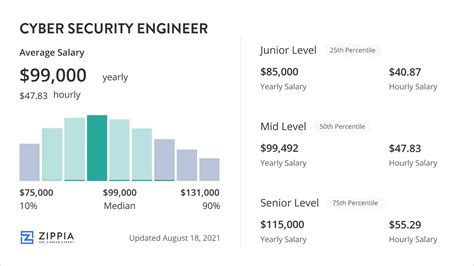
This is the central question, and the answer is multifaceted. A master's degree in cybersecurity acts as a significant financial multiplier throughout your career. While headlines often quote a single average, the reality is a wide spectrum influenced by your specific role, experience, and other factors we'll discuss next.
Let's ground our analysis in data from trusted sources. The U.S. Bureau of Labor Statistics (BLS), in its May 2022 data (the most recent comprehensive report), stated the median annual wage for Information Security Analysts was $112,000. The top 10 percent earned more than $174,690. Importantly, the BLS notes that "many employers require analysts to have experience in a related occupation," and a master's degree is often a key qualifier for the higher-paying, senior-level positions within this category.
However, "Information Security Analyst" is a broad term. To get a more granular view that reflects the impact of a master's degree, we turn to industry-specific salary aggregators.
- Payscale.com reports that the average salary for a professional with a Master of Science (MS), Cyber Security degree is approximately $101,000 per year (data accessed October 2023). This figure is an aggregate across various job titles and experience levels.
- Salary.com provides a more role-specific view. For a Cyber Security Manager, the median salary in the U.S. is $144,357, with the typical range falling between $132,152 and $158,162 (data accessed October 2023). It's in these managerial roles where a master's degree becomes a common, and often required, credential.
- Glassdoor reports a national average base salary for a "Cyber Security Engineer" at $116,589 per year, with a likely range from $91k to $150k (data accessed October 2023).
These numbers tell a clear story: earning a master's degree in cybersecurity firmly places you in the six-figure salary club. But to truly understand your potential, we must break it down by experience level. A graduate fresh from their master's program (but with some prior IT experience) will earn differently than a 10-year veteran moving into a director role.
### Cybersecurity Salary by Experience Level (with a Master's Degree)
| Experience Level | Common Job Titles | Typical Base Salary Range | Total Compensation Insights |
| ---------------- | ------------------------------------------------- | ----------------------------- | ----------------------------------------------------------------------------------------------------------------------- |
| Entry-Level (0-2 years post-Master's) | Cyber Security Analyst, Security Consultant, Jr. Penetration Tester, Security Engineer | $85,000 - $115,000 | Base salary is the main component. May include a modest annual performance bonus (3-7%) or a small signing bonus. |
| Mid-Career (3-7 years) | Senior Security Engineer, Security Architect, Incident Response Lead, Cloud Security Specialist | $115,000 - $160,000 | Bonuses become more significant (8-15%). In tech companies, Restricted Stock Units (RSUs) begin to form a meaningful part of total compensation. |
| Senior/Managerial (8-15 years) | Security Manager, Director of Security, Principal Security Architect, GRC Manager | $160,000 - $220,000+ | Substantial bonuses (15-25%+) and significant equity grants (RSUs) are common, pushing total compensation much higher than base salary. |
| Executive (15+ years) | Chief Information Security Officer (CISO), VP of Security | $220,000 - $400,000+ | Base salary may cap around $250k-$300k, but total compensation, driven by massive equity packages and executive bonuses, can reach $500k or more. |
_Source: Data synthesized from Payscale, Salary.com, Glassdoor, and the 2022 (ISC)² Cybersecurity Workforce Study._
### Beyond the Base Salary: Deconstructing Your Total Compensation
In the world of technology and security, your base salary is only one piece of the puzzle. Understanding the full compensation package is crucial for evaluating job offers and maximizing your lifetime earnings.
- Performance Bonuses: These are annual bonuses tied to your individual performance and the company's success. In cybersecurity, this can be linked to metrics like reduction in security incidents, successful project completion, or audit results. For senior roles, this can be a significant percentage of your base salary.
- Restricted Stock Units (RSUs) & Stock Options: Particularly prevalent in publicly traded tech companies and promising startups, equity is a massive wealth-building tool. RSUs are grants of company stock that vest over a period (typically 4 years). This means that a base salary of $150,000 could be part of a total compensation package worth over $220,000 when you factor in $70,000 worth of stock vesting that year. This is a primary reason why salaries at major tech firms often appear astronomically high.
- Signing Bonuses: To attract top talent, especially those with advanced degrees and in-demand skills, companies often offer a one-time signing bonus. This can range from $5,000 for a junior role to over $50,000 for a senior, highly sought-after specialist. It's a powerful negotiation tool.
- Profit Sharing: Some companies distribute a portion of their profits to employees. This is common in more established, non-tech industries and consulting firms.
- Benefits: Never underestimate the value of a strong benefits package. This includes top-tier health, dental, and vision insurance; a generous 401(k) match (which is essentially free money); and ample paid time off. Furthermore, a key benefit in this field is a professional development budget. Many leading companies will pay for you to attend conferences like Black Hat or DEF CON and cover the cost of expensive certifications (like the CISSP or SANS courses), which can be worth tens of thousands of dollars.
When evaluating a masters in cyber security salary, you must learn to think in terms of Total Compensation. An offer with a slightly lower base salary but a massive equity grant and a strong 401(k) match could be far more lucrative in the long run.
Key Factors That Influence Your masters in cyber security salary
Your master's degree is your launchpad, but several other factors will determine the altitude your career—and salary—will reach. In my experience as a career analyst, these are the levers that professionals can actively pull to steer their compensation upwards. Mastering them is the key to unlocking your full earning potential.
### 1. Level of Education & Certifications: The One-Two Punch
While this article focuses on the master's degree, it's essential to understand its place in the educational hierarchy and how it synergizes with industry certifications.
- Bachelor's vs. Master's: The data consistently shows a clear salary premium for holding a master's degree. Payscale's data suggests this premium can be between 10% and 20% for comparable roles and experience levels. Why? A master's curriculum delves into topics often omitted from undergraduate programs: strategic risk management, advanced cryptography, security policy and law, and leadership. This prepares you for management-track roles sooner, leading to faster salary progression. Furthermore, many elite government and Fortune 500 roles explicitly list a master's degree as a "preferred" or even "required" qualification for senior positions.
- The Power of Certifications: In cybersecurity, certifications are not just resume-boosters; they are validated proof of specific skills and are often used by HR systems to filter candidates. A master's degree proves your theoretical and strategic knowledge; a certification proves your hands-on, technical prowess. The combination is what makes you an elite candidate.
Key Certifications and Their Salary Impact:
- (ISC)² Certified Information Systems Security Professional (CISSP): This is the gold standard for security managers and leaders. It is not a technical certification but a comprehensive measure of your knowledge across eight critical domains. The (ISC)² Workforce Study consistently shows that certified professionals earn significantly more than their non-certified counterparts. Holding a CISSP can add $15,000 to $25,000 or more to your annual salary. It's often a hard requirement for any role with "Manager" or "Director" in the title.
- ISACA Certified Information Security Manager (CISM): Similar to the CISSP but with a stronger focus on governance and program management. It's ideal for those who want to move into GRC (Governance, Risk, and Compliance) or CISO-track roles. The salary impact is comparable to the CISSP.
- Offensive Security Certified Professional (OSCP): For those specializing in penetration testing, this is the ultimate hands-on certification. It requires passing a grueling 24-hour practical exam. An OSCP is a signal of elite technical skill and can easily add a $20,000+ premium to a penetration tester's salary.
- SANS/GIAC Certifications (e.g., GCIH, GCFA, GPEN): The SANS Institute offers highly respected, specialized training and certifications. A GIAC Certified Incident Handler (GCIH) or GIAC Certified Forensic Analyst (GCFA) can significantly boost the salary for incident response and forensics professionals. These courses are expensive, which is why having an employer pay for them is a major perk.
- Cloud Certifications (e.g., AWS Certified Security - Specialty, Azure Security Engineer Associate): With nearly every company moving to the cloud, certified cloud security skills are arguably the hottest commodity in the market right now. Possessing these certifications can open doors to roles with base salaries starting at $140,000+, even for mid-career professionals.
### 2. Years of Experience: The Upward Trajectory
Experience is the single most powerful driver of salary growth over time. Your master's degree accelerates this journey, allowing you to compress the timeline. Here’s a more detailed breakdown of the career and salary arc:
- Phase 1: The Foundation (0-2 years post-Master's). Salary: $85k - $115k. You're likely in a "Level II" analyst or engineer role. You've bypassed the most junior positions thanks to your degree. Your focus is on applying your academic knowledge to real-world scenarios, mastering core security tools (like SIEMs, EDRs), and proving your value on a team.
- Phase 2: The Specialist (3-7 years). Salary: $115k - $160k. You are now a trusted, senior member of the team. You've likely specialized in an area like cloud security, incident response, or application security. You're leading small projects, mentoring junior analysts, and are the go-to person for a specific technology or process. Your total compensation package now includes meaningful equity or larger bonuses.
- Phase 3: The Leader (8-15 years). Salary: $160k - $220k+. This is where the master's degree truly pays off. You transition from "doing" to "leading." You're now a Security Manager, Director, or a Principal Architect. Your job is about managing budgets, hiring talent, setting strategic direction, and communicating risk to the C-suite. Your compensation is heavily weighted towards performance bonuses and stock.
- Phase 4: The Executive (15+ years). Salary: $220k - $400k+ (Total Comp often > $500k). You've reached the pinnacle: CISO or VP of Security. Your responsibility now spans the entire organization. You are a business executive who specializes in security. Your success is measured by the organization's resilience and your ability to enable the business to take smart risks.
### 3. Geographic Location: Where You Work Matters
Your physical (or remote) location plays a massive role in your salary due to variations in demand and cost of living.
Top-Paying Metropolitan Areas for Cybersecurity Professionals:
1. San Jose-Sunnyvale-Santa Clara, CA (Silicon Valley): The epicenter of the tech world. Salaries here are the highest in the nation, but so is the cost of living. A senior security engineer can command $180,000 - $250,000+ in base salary alone.
2. Washington-Arlington-Alexandria, DC-VA-MD: This region is a hub for government and defense contracting work. High demand for cleared professionals drives salaries up. Expect salaries to be 15-25% higher than the national average, especially for roles requiring a security clearance.
3. New York-Newark-Jersey City, NY-NJ-PA: The financial capital of the world has an insatiable demand for security professionals to protect trillions of dollars in assets. Top-tier salaries are common, often approaching Silicon Valley levels.
4. Seattle-Tacoma-Bellevue, WA: Home to Microsoft and Amazon, this is another major tech hub with competitive salaries and a high cost of living.
5. Austin-Round Rock, TX & Dallas-Fort Worth, TX: Texas is a rapidly growing tech hub with a lower cost of living than the coasts, making it an attractive destination. While base salaries might be slightly lower than in SF or NYC, your purchasing power can be significantly greater.
The Rise of Remote Work: The pandemic permanently altered the landscape. Many companies now hire cybersecurity talent remotely. This has created two competing trends:
- Location-Based Pay: Some companies adjust your salary based on the cost of living in your city.
- National Rate Pay: Other companies, particularly those competing for top talent, offer a single competitive salary regardless of where you live. This can provide a massive financial advantage if you can earn a "San Francisco" salary while living in a lower-cost area. As a candidate, this is a key point of negotiation.
### 4. Company Type & Size: Who You Work For
The type of organization you work for has a profound impact on your salary, work-life balance, and career trajectory.
- Big Tech (FAANG - Facebook/Meta, Amazon, Apple, Netflix, Google): These companies offer the highest compensation packages, period. The combination of high base salaries, massive RSU grants, and generous bonuses is unmatched. The work is cutting-edge, but the environment is often highly demanding and competitive.
- Large Corporations (Fortune 500 - Finance, Healthcare, Retail): These companies offer very competitive and stable salaries. The focus is often on risk management, compliance, and securing massive, complex legacy systems. The pace may be slower than in Big Tech, but the benefits and job security are typically excellent.
- Cybersecurity Vendors & Consulting Firms: Working for a company that *sells* security (e.g., CrowdStrike, Palo Alto Networks) or a consulting firm (e.g., Deloitte, Mandiant) can be very lucrative. You get to work on diverse and challenging problems for multiple clients. The hours can be long, and travel may be required, but the learning and earning potential are immense.
- Startups: This is the high-risk, high-reward path. Your base salary will likely be lower than at a large corporation. The tradeoff is a significant grant of stock options or equity. If the startup succeeds, this equity could be worth millions. You'll wear many hats and gain incredible experience quickly, but you'll also face uncertainty and long hours.
- Government & Public Sector: Working for an agency like the NSA, FBI, or DHS will mean a lower base salary than in the private sector. However, the tradeoff is significant: unparalleled job security, excellent federal benefits, a pension plan, and the opportunity to work on mission-critical national security challenges. A security clearance obtained in a government role is also extremely valuable and can lead to high-paying contracting jobs later in your career.
### 5. Area of Specialization: The Key to Premium Pay
Cybersecurity is not a monolithic field. Your master's program will likely allow you to specialize, and choosing the right specialization can dramatically increase your salary.
High-Demand, High-Salary Specializations:
- Cloud Security: As mentioned, this is arguably the most in-demand specialty. Professionals who can secure AWS, Azure, and Google Cloud environments are in a constant bidding war.
- Application Security (AppSec / DevSecOps): This involves embedding security into the software development lifecycle. Professionals who can speak the language of developers, automate security testing in CI/CD pipelines, and secure code are highly prized.
- Offensive Security (Penetration Testing / Red Teaming): Ethical hackers who can think like an adversary and uncover critical vulnerabilities before the real attackers do will always command a premium.
- Incident Response & Digital Forensics (DFIR): These are the high-stakes, high-pressure roles. When a major breach happens, these are the first responders. Experienced DFIR leads who can manage a crisis are invaluable.
- Identity and Access Management (IAM): In a world of zero-trust architecture, managing who has
